14) which of the following are breach prevention best practices
Developing the IRP will help the IT staff of the company to control the data breach incidents. Invest in security automation.

14 Top Data Security Risks Every Business Should Address
Invest in the Right Security.

. Phases of a data breach reported data breaches data breach laws best practices. Which of the following are breach prevention best practices. Invest in security automation.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your. Create Strong Policies Strong Passwords. 30 Best Practices for Preventing a Data Breach.
The following are high-level best practices for preventing breaches. Best Practices For Prevention And Immediate Response To A Breach. However these 30 best practices for preventing a data breach can.
Identity sensitive data collected stored transmitted or processes. Properly configure the cloud. Companies that leveraged artificial intelligence machine learning.
The following are high-level best practices for preventing breaches. Making weak passwords can be a reason for Data. Vulnerability assessment is the process intended to identify classify and prioritize security threats and.
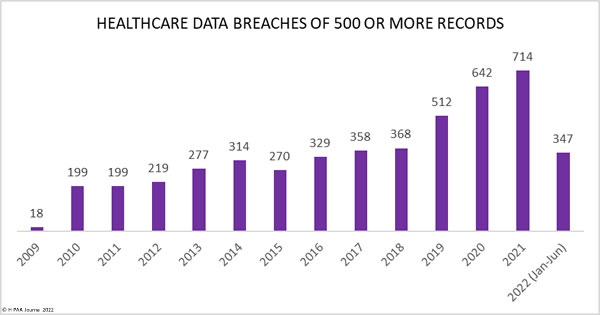
2 data breach landscape data breaches cost companies an average of 221 per. Employees have an important role in keeping their organizations secure. 11 Which of the following are breach prevention best practices.
Companies take steps to apply data. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022. Which of the following are examples of personally identifiable information PII.
Identify areas that store transmit collect or process. Which of the following are breach. In the age of digital data keeping information safe is more important than ever.
Which of the following are breach prevention best practices. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more. Which of the following are breach prevention best practices.
Implementing encryption standards and backup policies to decrease risks and make sure that software is up. Which of the following are breach prevention best practices. Which are breach prevention best practices.
In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. A breach as defined by the DoD is broader than. All of this above.
In which of the following. Data encryption solutions to render data inaccessible and unusable in. In a hyper-connected business world organizational leaders understand that data breaches are a fact of life.
Data loss protection DLP to detect and prevent data breaches by blocking the extraction of sensitive information. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business. The employees play an essential responsibility in keeping their companies safe.
Best Practices for Preventing a Data BreachTrain Employees on Security Awareness.
5 Best Practices For Data Breach Prevention Endpoint Protector

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

What Is Cybersecurity Definition Importance Threats And Best Practices Spiceworks It Security
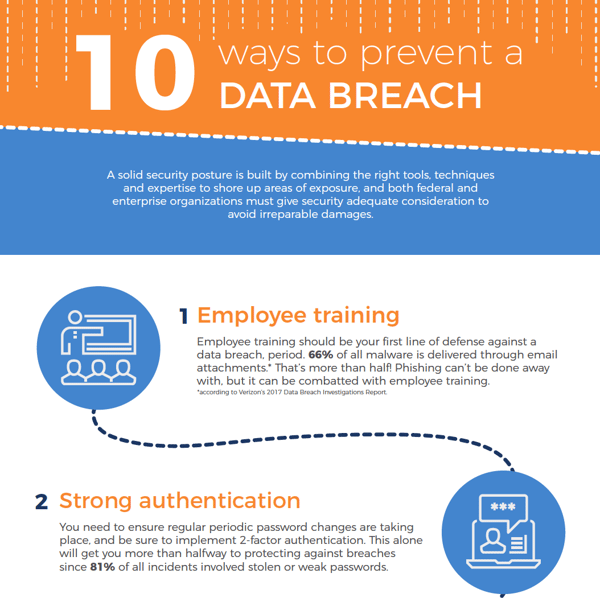
10 Ways To Prevent A Data Breach

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System
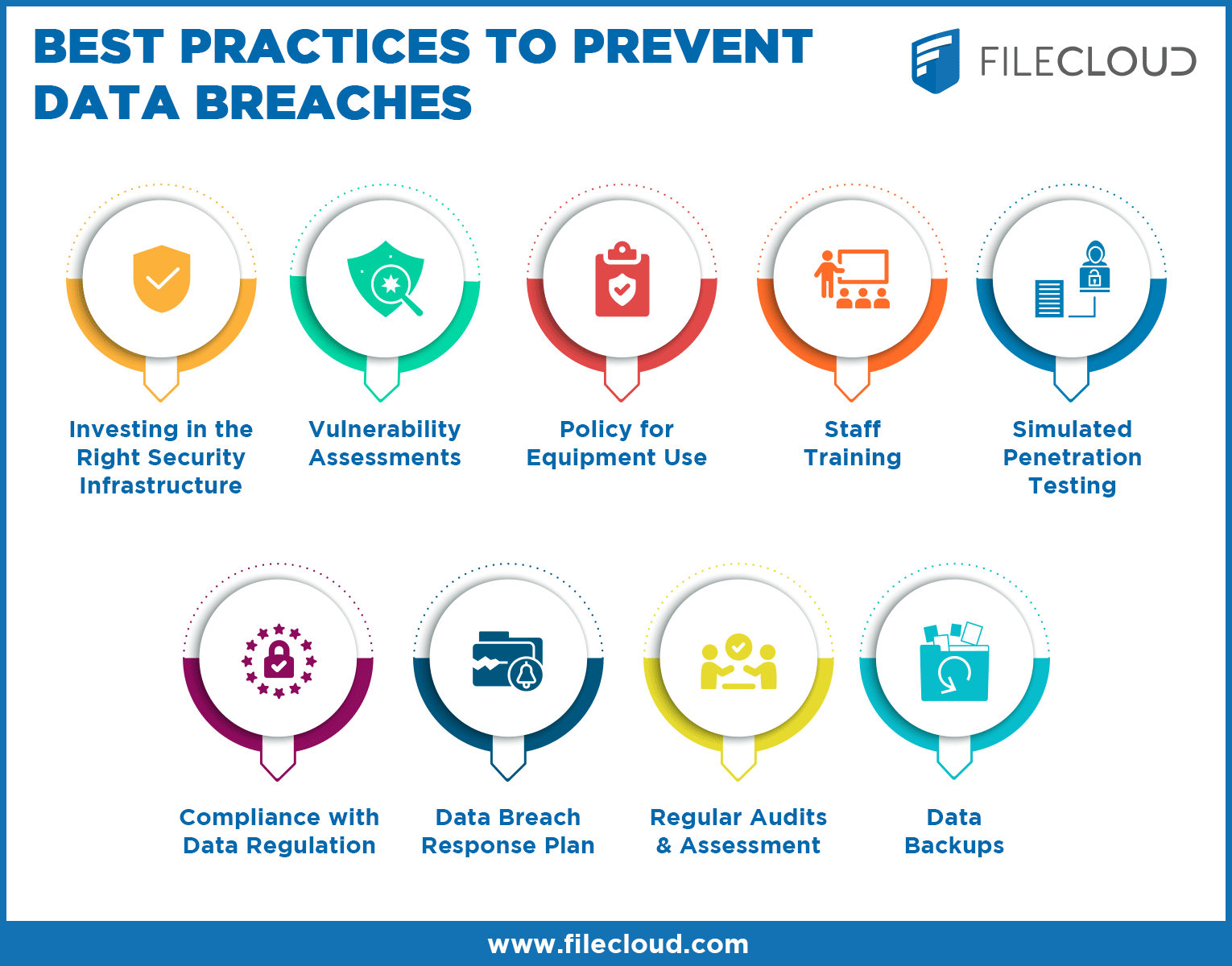
Tips For Data Leakage And Breach Prevention Filecloud
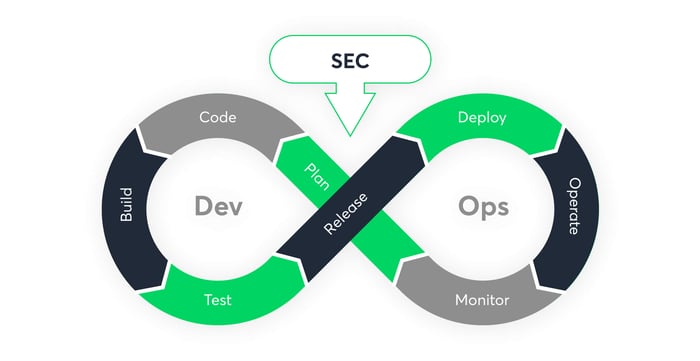
Devops Security Best Practices Protect Your Apps From Vulnerabilities

101 Data Protection Tips How To Keep Your Passwords Financial Personal Information Online Safe In 2022 Digital Guardian
Board Oversight Of Cyber Risks And Cybersecurity

30 Best Practices For Preventing A Data Breach Securityscorecard

The Best Crisis Management Examples Smartsheet

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire

6 Most Common Causes Of Data Leaks In 2022 Upguard

Solutions Cisco Breach Defense Design Guide Cisco
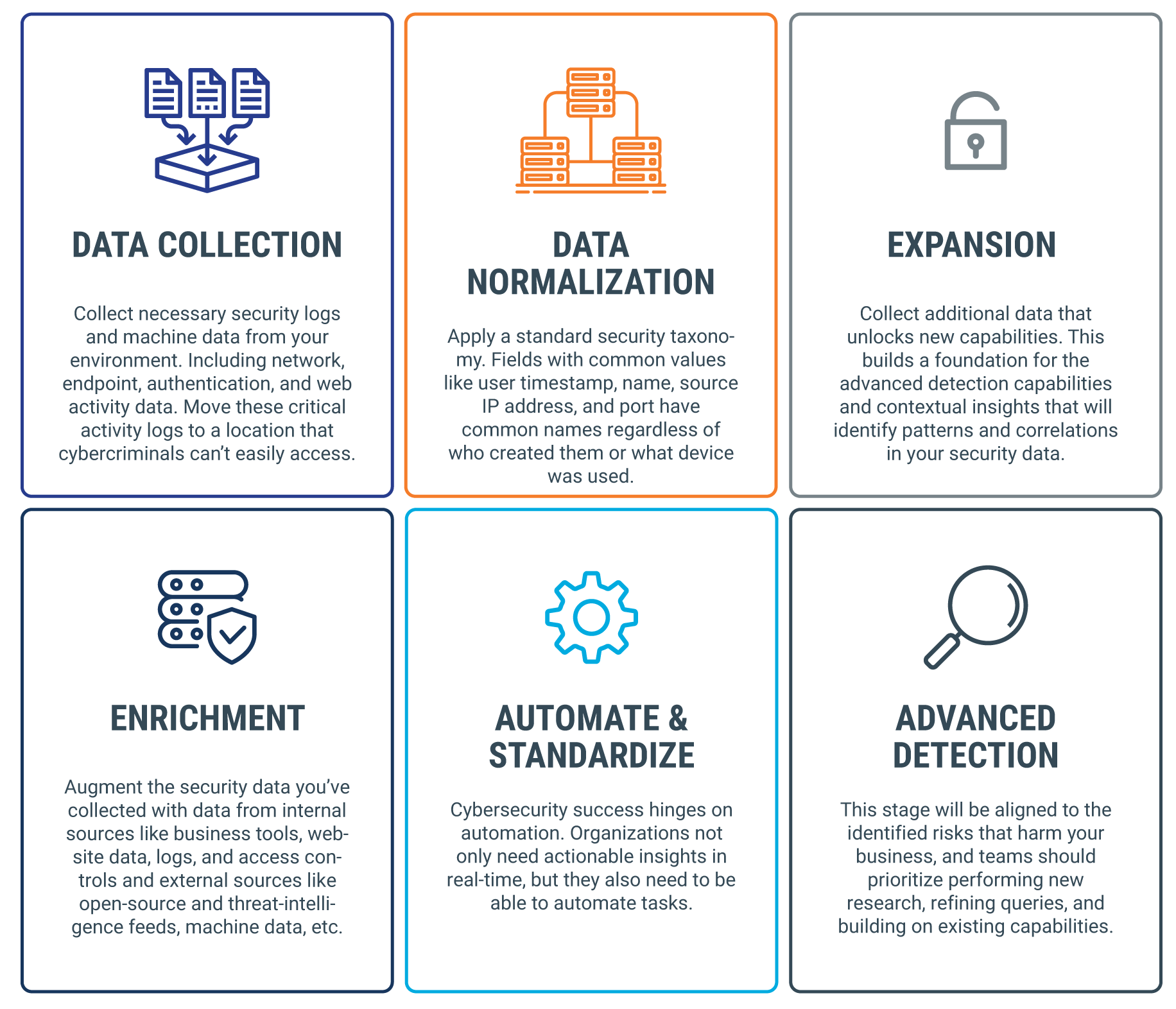
Data Analytics Cybersecurity Best Practices 3pillar Global

Cis Control 14 Security Awareness And Skills Training